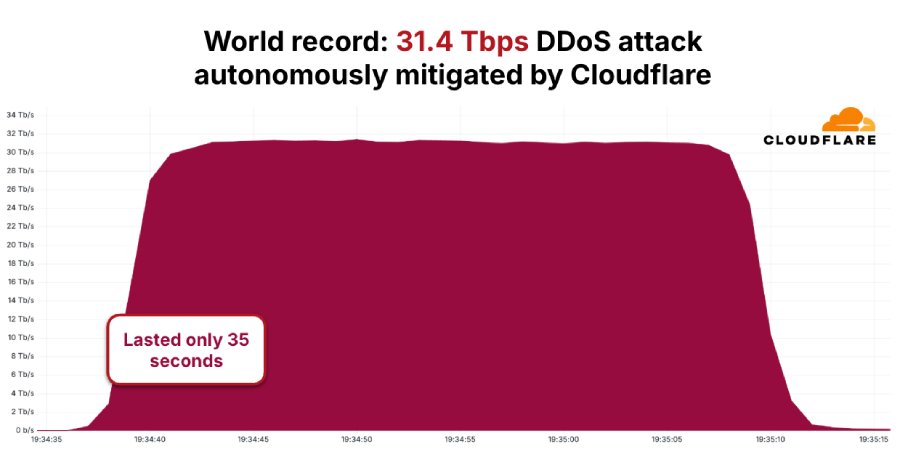

The distributed denial-of-service (DDoS) botnet generally known as AISURU/Kimwolf has been attributed to a record-setting assault that peaked at 31.4 Terabits per second (Tbps) and lasted solely 35 seconds.
Cloudflare, which routinely detected and mitigated the exercise, stated it is a part of a rising variety of hyper-volumetric HTTP DDoS assaults mounted by the botnet within the fourth quarter of 2025. The assault befell in November 2025.
AISURU/Kimwolf has additionally been linked to a different DDoS marketing campaign codenamed The Evening Earlier than Christmas that commenced on December 19, 2025. Per Cloudflare, the common measurement of the hyper-volumetric DDoS assaults throughout the marketing campaign was 3 billion packets per second (Bpps), 4 Tbps, and 54 requests per second (Mrps), with the utmost charges touching 9 Bpps, 24 Tbps, and 205 Mrps.
“DDoS assaults surged by 121% in 2025, reaching a median of 5,376 assaults routinely mitigated each hour,” Cloudflare’s Omer Yoachimik and Jorge Pacheco stated. “In 2025, the entire variety of DDoS assaults greater than doubled to an unimaginable 47.1 million.”
The online infrastructure firm famous that it mitigated 34.4 million network-layer DDoS assaults in 2025, in comparison with 11.4 million in 2024. In This autumn 2025 alone, network-layer DDoS assaults accounted for 78% of all DDoS assaults. Put collectively, the variety of DDoS assaults surged by 31% over the earlier quarter and 58% over 2024.
In 2025 This autumn, hyper-volumetric assaults elevated by 40% in comparison with the earlier quarter, witnessing a leap from 1,304 to 1,824. A complete of 717 assaults have been recorded in Q1 2025. The spike within the variety of assaults has been complemented by an uptick within the measurement of those assaults, rising by over 700% in comparison with the big assaults seen in late 2024.

AISURU/Kimwolf has ensnared greater than 2 million Android gadgets, most of that are compromised, off-brand Android TVs, into its botnet, usually by tunneling by means of residential proxy networks like IPIDEA. Final month, Google disrupted the proxy community and initiated authorized motion to take down dozens of domains used to regulate gadgets and proxy visitors by means of them.
It additionally partnered with Cloudflare to disrupt IPIDEA’s area decision, impacting their capacity to command and management contaminated gadgets and market their merchandise.
IPIDEA is assessed to have enrolled gadgets utilizing no less than 600 trojanized Android apps that embedded numerous proxy software program growth kits (SDKs), and over 3,000 trojanized Home windows binaries posing as OneDriveSync or Home windows updates. Moreover, the Beijing-based firm has marketed a number of VPN and proxy apps that silently turned customers’ Android gadgets into proxy exit nodes with out their information or consent.
What’s extra, the operators have been discovered to run no less than a dozen residential proxy companies that masquerade as legit providers. Behind the scenes, all these choices are linked to a centralized infrastructure that is beneath the management of IPIDEA.
A number of the different noteworthy traits noticed by Cloudflare throughout This autumn 2025 are as follows –
- Telecommunications, service suppliers, and carriers emerged as essentially the most attacked sector, adopted by data know-how, playing, gaming, and pc software program verticals.
- China, Hong Kong, Germany, Brazil, the U.S., the U.Ok., Vietnam, Azerbaijan, India, and Singapore have been essentially the most attacked international locations.
- Bangladesh surpassed Indonesia to turn out to be the most important supply of DDoS assaults. Different high sources included Ecuador, Indonesia, Argentina, Hong Kong, Ukraine, Vietnam, Taiwan, Singapore, and Peru.
“DDoS assaults are quickly rising in sophistication and measurement, surpassing what was beforehand possible,” Cloudflare stated. “This evolving risk panorama presents a big problem for a lot of organizations to maintain tempo. Organizations presently counting on on-premise mitigation home equipment or on-demand scrubbing facilities could profit from re-evaluating their protection technique.”