
An modern method to discovering, analyzing, and governing id utilization past conventional IAM controls.
The Problem: Identification Lives Exterior the Identification Stack
Identification and entry administration instruments have been constructed to control customers and directories.
Trendy enterprises run on purposes. Over time, id logic has moved into utility code, APIs, service accounts, and customized authentication layers. Credentials are embedded. Authorization is enforced domestically. Utilization patterns change with out overview.
These id paths usually function outdoors the visibility of IAM, PAM, and IGA.
For safety and id groups, this creates a blind spot – what we name Identification Darkish Matter.
This darkish matter is answerable for the id threat that can’t be instantly noticed.
Why Conventional Approaches Fall Quick
Most id instruments depend on configuration knowledge and coverage fashions.
That works for managed customers.
It doesn’t work for:
- Customized-built purposes
- Legacy authentication logic
- Embedded credentials and secrets and techniques
- Non-human identities
- Entry paths that bypass id suppliers
Because of this, groups are left reconstructing id habits throughout audits or incident response.
This method doesn’t scale. Learn to uncover this invisible layer of identity.
Orchid’s Approach: Discover, Analyze, Orchestrate, Audit
Orchid Security addresses this gap by providing continuous identity observability across applications. The platform follows a four-stage operational model aligned to how security teams work.
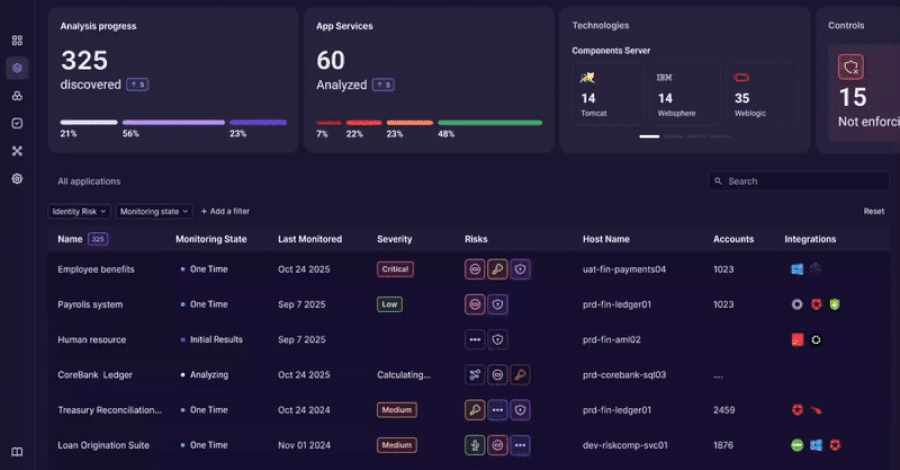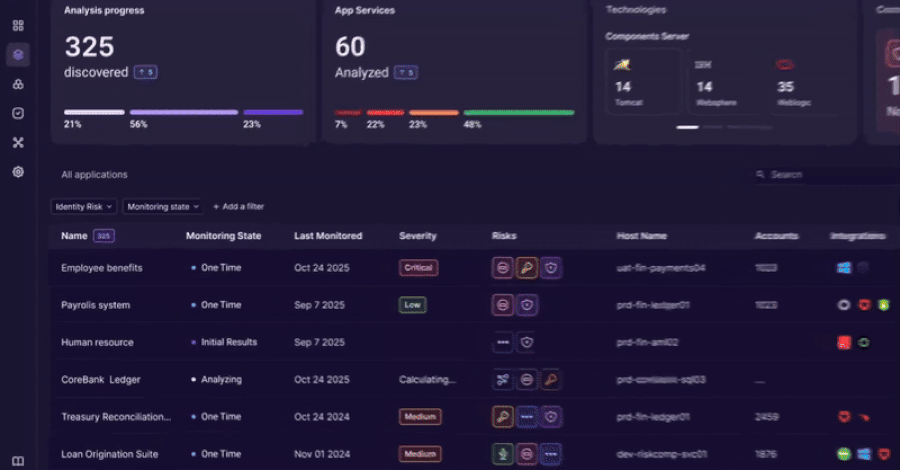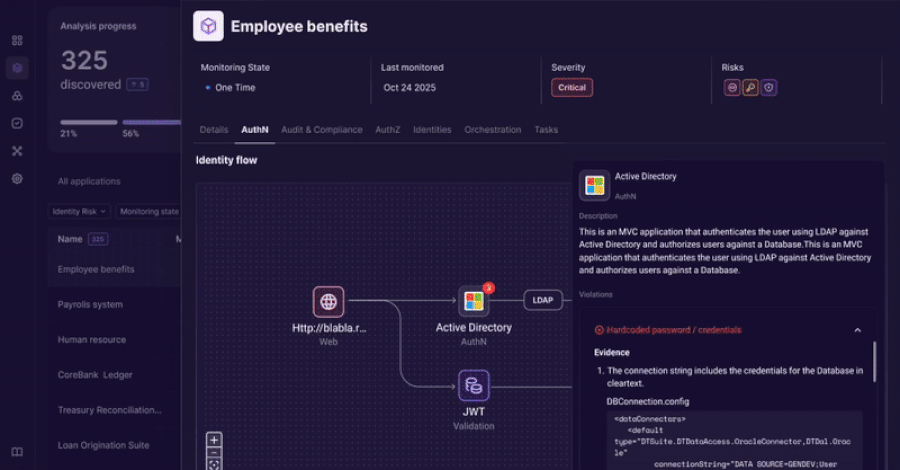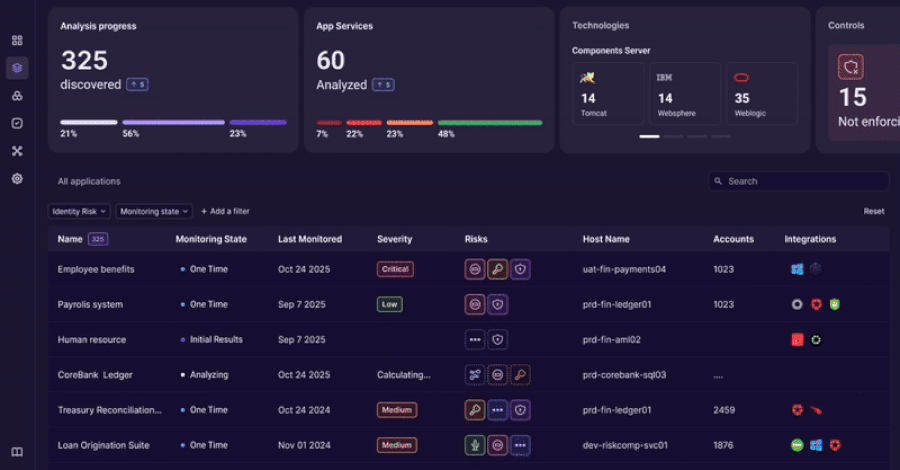
Discover: Identify Identity Usage Inside Applications
Orchid begins by discovering applications and their identity implementations.
Lightweight instrumentation analyzes applications directly to identify authentication methods, authorization logic, and credential usage.
This discovery includes both managed and unmanaged environments.
Teams gain an accurate inventory of:
- Applications and services
- Identity types in use
- Authentication flows
- Embedded credentials
This establishes a baseline of identity activity across the environment.

Analyze: Assess Identity Risk Based on Observed Behavior
Once discovery is complete, Orchid analyzes identity usage in context.
The platform correlates identities, applications, and access paths to surface risk indicators such as:
- Shared or hardcoded credentials
- Orphaned service accounts
- Privileged access paths outside IAM
- Drift between intended and actual access
Analysis is driven by observed behavior rather than assumed policy.
This allows teams to focus on identity risks that are actively in use.



Orchestrate: Act on Identity Findings
With analysis complete, Orchid enables teams to take action.
The platform integrates with existing IAM, PAM, and security workflows to support remediation efforts.
Teams can:
- Prioritize identity risks by impact
- Route findings to the appropriate control owner
- Track remediation progress over time
Orchid does not replace existing controls. It coordinates them using an accurate identity context.

Audit: Maintain Continuous Evidence of Identity Control
Because discovery and analysis run continuously, audit data is always available.
Security and GRC teams can access:
- Current application inventories
- Evidence of identity usage
- Documentation of control gaps and remediation actions
This reduces reliance on manual evidence collection and point-in-time reviews.
Audit becomes an ongoing process rather than a periodic scramble.


Practical Outcomes for Security Teams
Organizations using Orchid gain:
- Improved visibility into application-level identity usage
- Reduced exposure from unmanaged access paths
- Faster audit preparation
- Clear accountability for identity risk
Most importantly, teams can make decisions based on verified data rather than assumptions. Learn more about how Orchid uncovers Identity Dark Matter.
A few final words
As identity continues to move beyond centralized directories, security teams need new ways to understand and govern access.
Orchid Security provides continuous identity observability across applications, enabling organizations to discover identity usage, analyze risk, orchestrate remediation, and maintain audit-ready evidence.
This approach aligns identity security with how modern enterprise environments actually operate.