In immediately’s digital panorama, encrypted site visitors is the norm—not the exception. Whereas encryption akin to Transport Layer Safety (TLS) 1.3 protects person privateness and knowledge integrity, it additionally presents a rising problem for safety groups: How do you defend in opposition to threats hidden inside encrypted site visitors with out overwhelming your programs?
The problem of encrypted DDoS assaults
Menace actors are all the time on the lookout for methods to bypass trendy defenses, and one of the vital common distributed denial-of-service (DDoS) assault strategies is to cover the assaults in what appears like extraordinary site visitors. Huge quantities of web site visitors now depend on Hypertext Switch Protocol Safe (HTTPS). Since decrypting TLS 1.3 site visitors sometimes requires proxy-based options—that are resource-intensive—many safety merchandise battle to examine encrypted classes successfully. This blind spot makes encrypted DDoS assaults tougher to detect and mitigate.
Block first, ask questions later
One approach to decrease the affect of encrypted assault site visitors is to easily drop it earlier than decrypting. There are a number of strategies we make use of to filter out the rubbish shortly and effectively:
- Identified supply blocking: Many attackers are actually utilizing open web proxies to cover the supply of their HTTPS assaults. We continually monitor these sources, and our ATLAS Intelligence Feed (AIF)-powered countermeasure can block them robotically.
- TLS assault prevention: This countermeasure appears on the TLS handshake (pre-encryption) and may block TLS classes that don’t observe normal person behaviors.
- TCP connection limiting: This countermeasure appears at TCP connection habits from every supply. Sources opening too many connections or partaking in abusive behaviors over TCP could be blocked.
- Charge-based protections: Normally, attackers will likely be sending extra site visitors than reputable customers, and these protections can distinguish and block these sources robotically.
- Selective decryption: That is used to decrypt and take care of more-advanced assaults, when encrypted site visitors habits mimics reputable customers.
Why full decryption isn’t all the time the reply
Decrypting all site visitors isn’t sensible. It’s computationally costly and may shortly exhaust system sources. What’s wanted is a better strategy—one which focuses decryption efforts solely the place it’s actually obligatory.
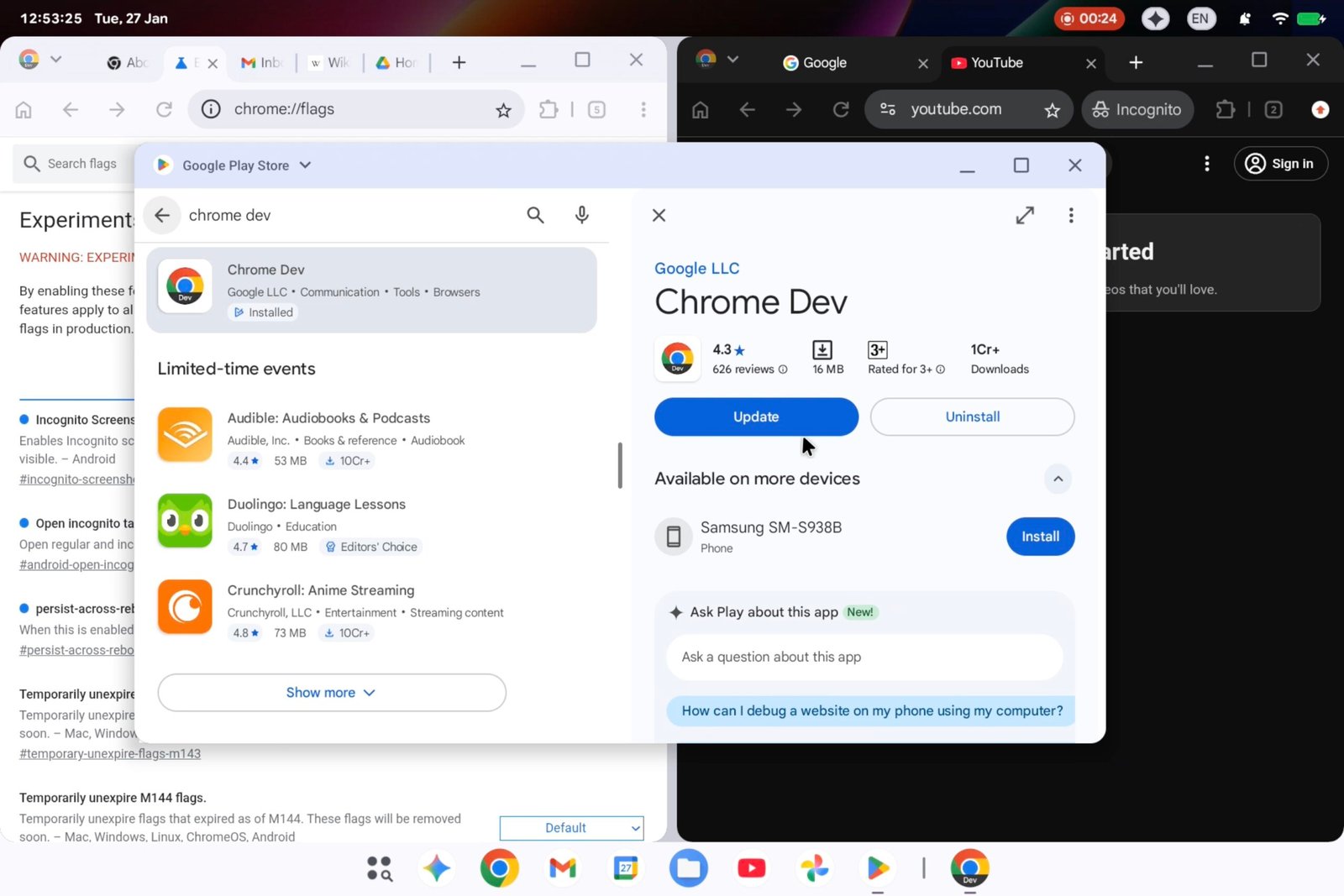
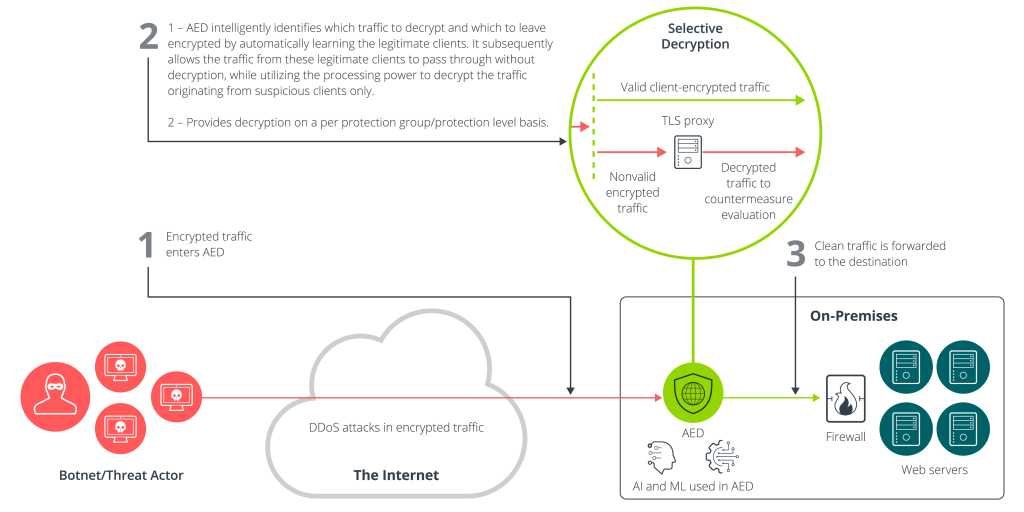
NETSCOUT’s resolution: Selective decryption
NETSCOUT’s Arbor Edge Protection (AED) provides a robust resolution through selective decryption. Positioned on the community edge, AED intelligently decides which site visitors to decrypt based mostly on risk indicators and consumer validation.
Right here’s the way it works:
- Clever decryption: Because the site visitors enters, AED identifies legitimate consumer site visitors and passes it on with out requiring decryption.
- Suspicious site visitors decryption: Solely non-validated encrypted site visitors is decrypted and analyzed for DDoS threats.
- Customizable decryption: Customers can allow decryption for particular safety teams or ranges, permitting focused inspection with out losing sources.
NETSCOUT
Advantages of choice decryption
Environment friendly useful resource use: Focuses decryption on suspicious site visitors, preserving system efficiency
Scalable safety: Allows high-scale protection in opposition to encrypted threats with out compromising throughput
Versatile configuration: Tailors decryption insurance policies to match the wants of various companies and risk ranges
Conclusion
As encrypted site visitors continues to develop, so does the necessity for smarter safety options. NETSCOUT AED’s selective decryption strategy empowers organizations to defend in opposition to encrypted DDoS assaults effectively and successfully—with out sacrificing efficiency.
Study extra about Arbor Edge Protection.