Right here’s how open-source intelligence helps hint your digital footprint and uncover your weak...
Security
As many as 3,136 particular person IP addresses linked to seemingly targets of the...
Bevor die Vorschläge der EU-Kommission umgesetzt werden und die Brüsseler Behörde damit tatsächlich weitreichendere...
Why what you are promoting wants the best-of-breed mixture of know-how and human experience...
Ravie LakshmananJan 20, 2026Cryptocurrency / Synthetic Intelligence A Telegram-based assure market identified for promoting...
“Attackers don’t have to know you’re utilizing it. They simply need to poke the...
Information publicity by high AI corporations, the Akira ransomware haul, Operation Endgame towards main...
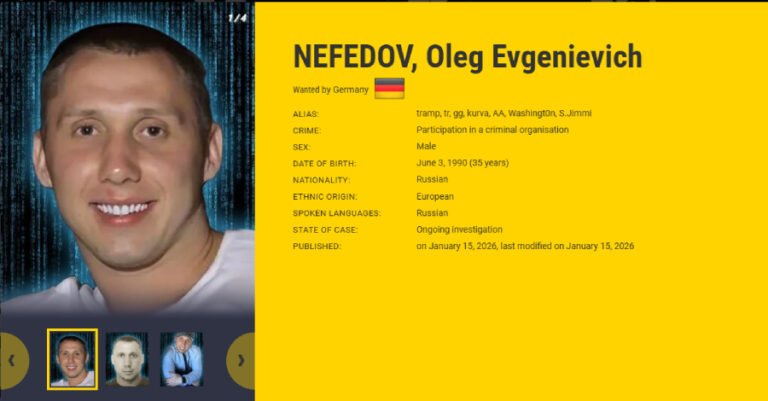
Ravie LakshmananJan 17, 2026Legislation Enforcement / Cybercrime Ukrainian and German regulation enforcement authorities have...
Exploitation was already noticed within the wild, with some intrusions resulting in WordPress Admin...
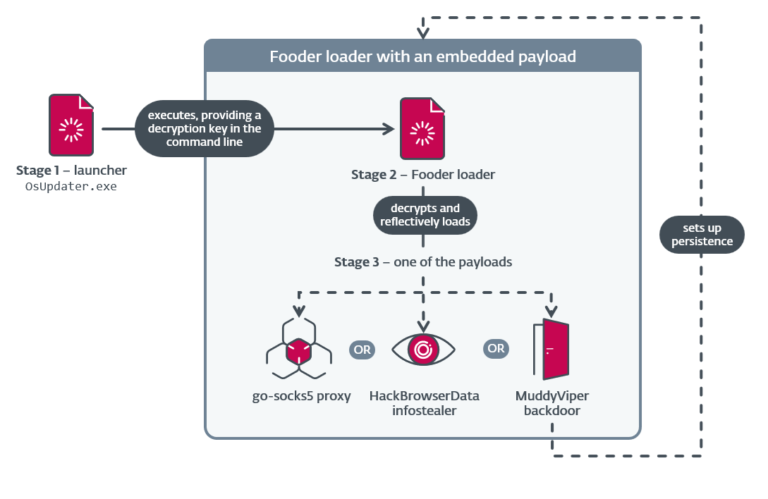
ESET researchers have recognized new MuddyWater exercise primarily focusing on organizations in Israel, with...